Do you desperately look for 'how to write hacking programs'? You can find all of the material on this webpage.
Table of contents
- How to write hacking programs in 2021
- Hacking with python for beginners
- How to create hacking tools using python
- How to make a hacking script
- Python hacking programs
- How to start hacking
- Password hacking program
- How hacking works
How to write hacking programs in 2021
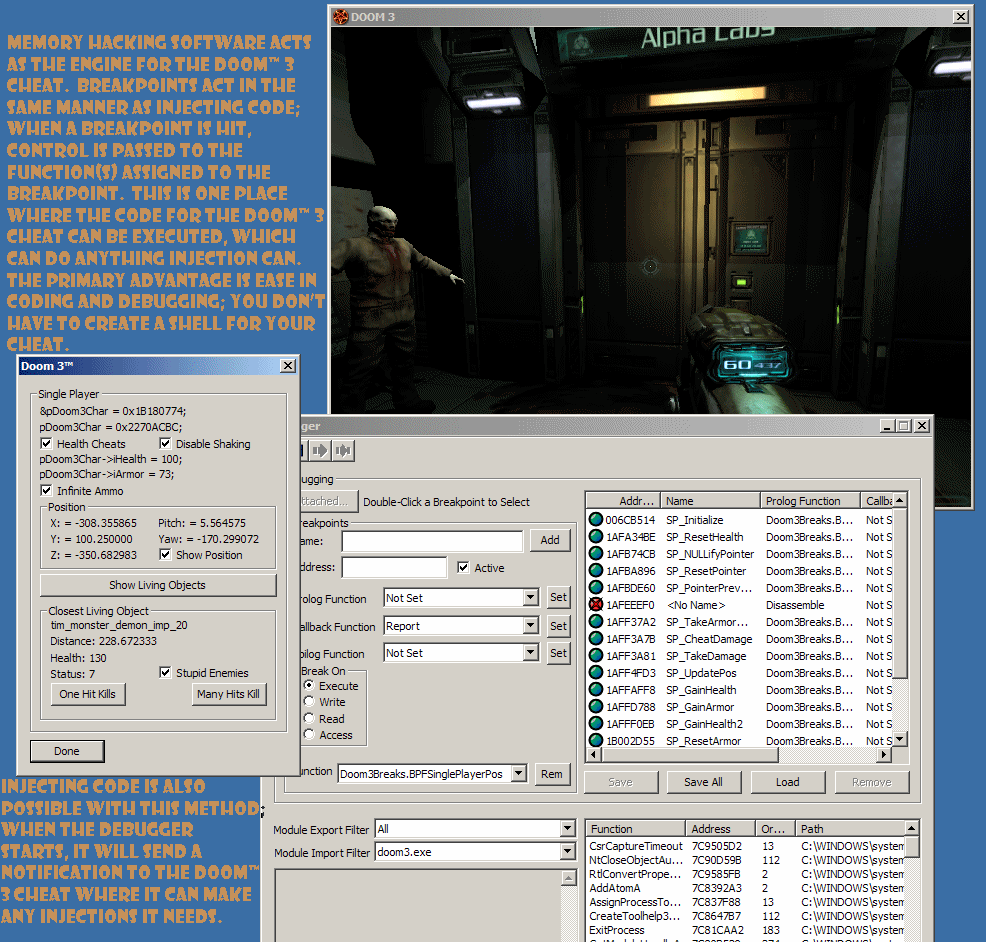 This image demonstrates how to write hacking programs.
This image demonstrates how to write hacking programs.
Hacking with python for beginners
 This image demonstrates Hacking with python for beginners.
This image demonstrates Hacking with python for beginners.
How to create hacking tools using python
 This image demonstrates How to create hacking tools using python.
This image demonstrates How to create hacking tools using python.
How to make a hacking script
 This image illustrates How to make a hacking script.
This image illustrates How to make a hacking script.
Python hacking programs
 This picture demonstrates Python hacking programs.
This picture demonstrates Python hacking programs.
How to start hacking
 This image shows How to start hacking.
This image shows How to start hacking.
Password hacking program
 This image shows Password hacking program.
This image shows Password hacking program.
How hacking works
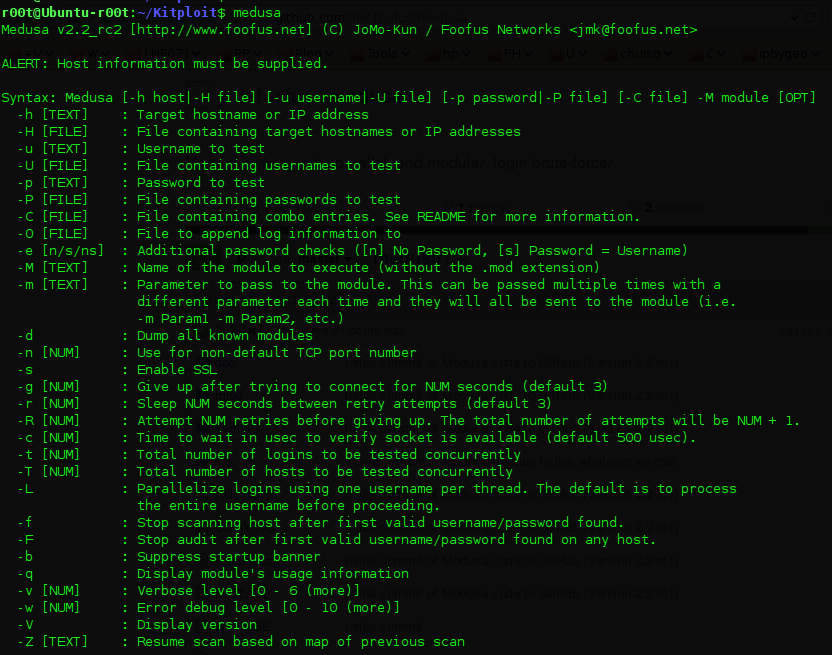 This picture shows How hacking works.
This picture shows How hacking works.
How to write and execute a simple, basic hacking code?
This is a keystrokes sequence well known as Konami Kode ( Code Konami — Wikipédia ). You will never make any harm using it, but just gain access to several easter eggs hidden in some apps or websites. Try randomly wherever you can, begin with some sample listed on Konami Code Sites ( Konami Code Sites) (Konami code required)
What kind of programs are used by hackers?
There are thousands of different programs hackers use to explore computers and networks. These programs give hackers a lot of power over innocent users and organizations -- once a skilled hacker knows how a system works, he can design programs that exploit it. Malicious hackers use programs to:
How can I become a free software hacker?
Steps Understand what software development requires. Know that anyone can become a free software hacker. Figure out your end goal. Determine a platform on which you want to work. Select a coding language. Get comfortable with the command line. Download and use Notepad++. Install a development environment. Start learning how to program.
Which is the best definition of a hacking tool?
A hacking tool is a computer program or software which helps a hacker to hack a computer system or a computer program. The existence of hacking tools has made the lives of hackers much simpler when compared to the times they did not exist. But it does not mean that if the Hacker is equipped with a good hacking tool, his entire job is smoothly done.
Last Update: Oct 2021
Leave a reply
Comments
Aliceann
25.10.2021 02:30Associate in Nursing ethical hacker exposes vulnerabilities in computer software to help business owners fix those security holes in front a malicious cyberpunk discovers them.